Deceive. Detect. Neutralize.
AI-first, preemptive protection
for Web, Cloud, IoT/OT & APIs —
stopping unseen threats before they breach.
Detect Earlier. Defend Smarter.
Web, Cloud & API protection that stops unseen threats before they spread.
See More. Decide Faster.
AI that cuts noise, exposes hidden attacks, and boosts SOC efficiency at scale.
Adapt Automatically. Everywhere.
Autonomous IoT/OT defense that adapts in real time to stop novel edge-born threats.
Nothreat Platform Prevents Attacks on Your Web Services and Devices in Real-time
Proven in the Real World. Measured in Outcomes.
Attacks blocked by a top-tier firewall
1x
without Nothreat
VS
Higher detection vs traditional tools
up to 11.2×
Attacks automatically blocked
99%+
Zero-days stopped before disclosure
40 days early
Build Your Preemptive Security
Pick the environments you want to protect. We'll scope the deployment and send a proposal tailored to your infrastructure.
Prebuilt Web Traps
Attract and expose real attackers with high-fidelity decoys that mirror common entry points without touching production.
Best for: VMware service / VPN / Firewall / Secure gateway / Other standard services
Prebuilt IoT/OT Traps
Detect lateral movement and edge threats early using realistic device decoys that generate actionable threat intelligence.
Best for: IP cameras / Network printers / PLC controllers / Other OT & IoT devices
Clone Your Services
Create digital twins of your critical production systems to detect and prevent unknown attacks before impacting real assets.
Best for: High-value bespoke Web Applications, APIs or IoT services
Real-time protection integrated with your existing cybersecurity stack
Using the Nothreat Platform and patented deception technology, we generate tailored real-time threat feeds to protect your genuine assets via your WAF and security stack. Stop zero-day attacks early with live dashboards and actionable intelligence.
8 traps selected

Purpose-Built Protection for Every Team & Use-Case
Flexible, Modular Protection — Pick What Your Business Needs
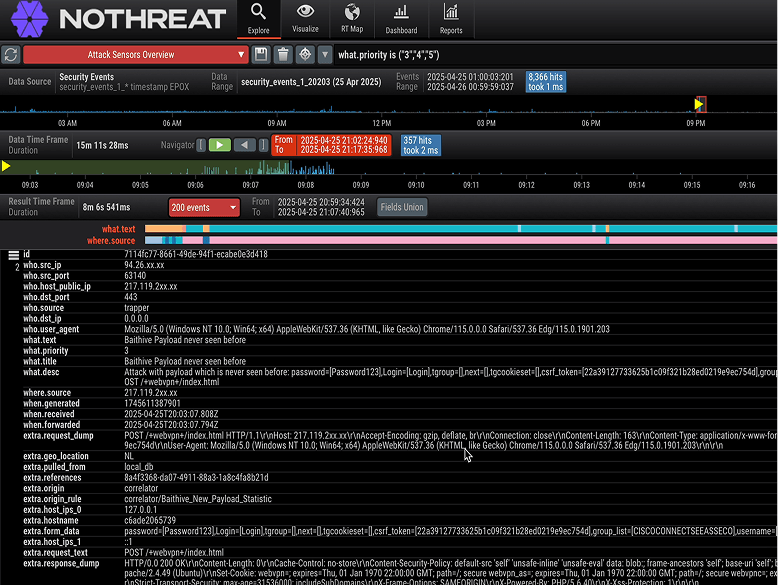
How Nothreat Works: The AI-First Security Model
A unified engine that detects earlier, reduces noise, and protects every environment automatically.
AI Threat Intelligence
Identify emerging threats before signatures exist.
Patented Deception
Expose attackers early with autonomous decoys.
On-Prem AI Analysis
Investigate faster with zero-cloud dependence.
Adaptive Protection
Secure Web, IoT/OT, APIs, and endpoints automatically.
Company news
 PressFebruary 02, 2026
PressFebruary 02, 2026Nothreat Partners with Andersen to Expand Enterprise Access to Preemptive Deception Technology
Nothreat helps enterprises stay ahead of cyber risk through AI-driven security solutions delivered in partnership with Andersen. By combining Nothreat’s preemptive deception technology with Andersen’s enterprise delivery capabilities, organisations gain early threat visibility, reduced risk, and continuous protection across complex digital environments. With Nothreat and Andersen, cybersecurity becomes a proactive, scalable, and strategic advantage.
 PressJanuary 14, 2026
PressJanuary 14, 2026Nothreat Collaborates with PASHA Bank to Strengthen AI-Driven Cybersecurity in Azerbaijan’s Financial Sector
Nothreat has partnered with PASHA Bank to deploy AI-driven cybersecurity across Azerbaijan’s financial sector, enabling proactive threat detection, real-time monitoring, and stronger digital resilience.

NothreatTM Threatscape 2025 Report
NothreatTM Threatscape 2025 Report
The web and Industrial IoT threat landscapes are no longer a game of simple probes and easily-detected malware. Our analysis of over 16 million automated attacks reveals a stark reality: the sheer volume of attacks is overwhelming, and the sophistication is rapidly increasing.




